
MICRO DEGREE
LIVE ClassesCybersecurity with GenAI Career Track
Become a professional Cybersecurity Specialist
in just 24 weeks!
Application closes on 02 Nov 2025
Become a professional Cybersecurity Specialist
in just 24 weeks!

100% Moneyback Guarantee
Reserve your spot today!
Basic Info
Select Offers
Application closes on:02 Nov 2025
Get instant access of pre-course material!
What is in it for you?
Transition to Cybersecurity role
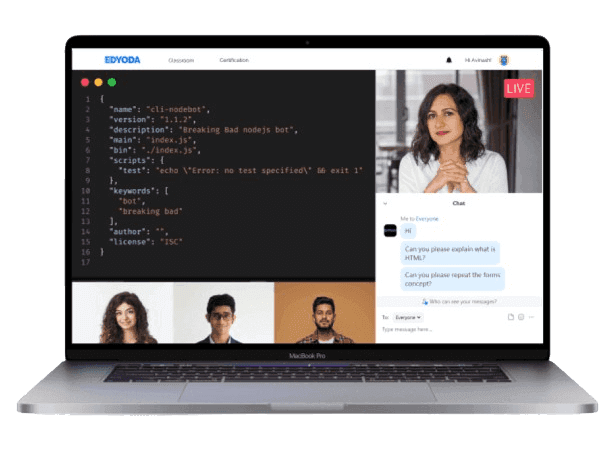
 Live Classes
Live Classes
 Instructor-led Live Sessions
Instructor-led Live Sessions
Attend 4 weeks of instructor led live classes at the lowest price ever
Projects & Case Studies
Projects & Case Studies
Gain hands-on experience with projects and real-world case studies for impactful learning
Verified Certificate
Verified Certificate
Earn a industry recognized certificate and kick start your career
Session Recordings
Session Recordings
Revisit older chapters anytime with recorded sessions
Lifetime Access
Lifetime Access of Recordings
Get lifetime access to the recorded sessions
Study Materials
Study Materials
Access comprehensive study materials designed to enhance your learning experience
Grab your slot before the offer expires
Discount applicable for next
10 candidates only
Grab your slot before the offer expires
Discount applicable for next 10 candidates only.
Reserve your spot today!
Basic Info
Select Offers
Application closes on:02 Nov 2025
Get instant access of pre-course material!
Dont just take our words
Trust our students







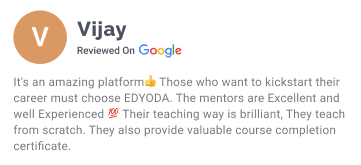


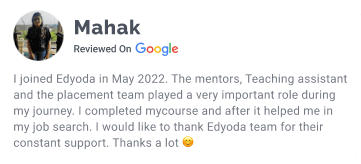


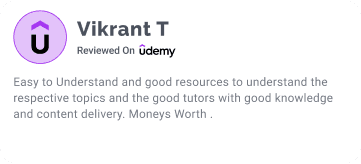

Career Track Journey
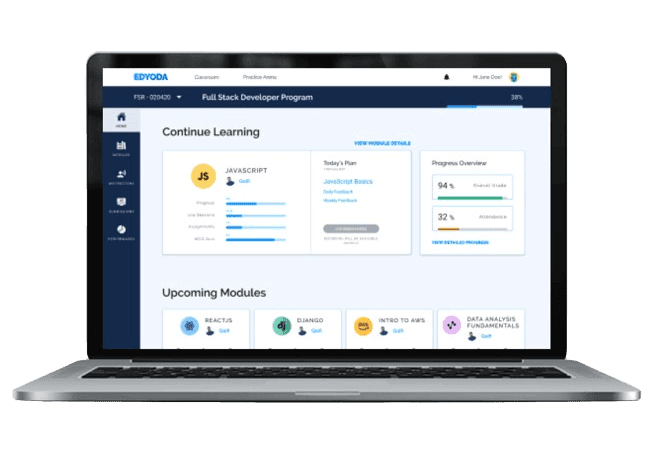
Curriculum
A Curriculum designed for your success
Live Sessions Schedule ![]() Sat - Sun (Weekends Only)
Sat - Sun (Weekends Only) ![]() Timing: 11:00 AM - 1:00 PM
Timing: 11:00 AM - 1:00 PM
Course Includes

Doubt Clearing Sessions

Relevant Assignments

Updated Study Materials

Live Projects
Your Instructors

Vibhuti S
13+ Years, CyberSecurity Sr. Manager, PayTm

Ankesh P
15+ Years, Cybersecurity Manager, Deloitte

S Ram
18+ Years, Sr. Architect, Microsoft
Tools Covered

Course Includes

Doubt Clearing Sessions

Relevant Assignments

Updated Study Materials

Live Projects
Course Pre-requisites
.ffb97545.png&w=16&q=75) Basic computer knowledge is required for this course.
Basic computer knowledge is required for this course..ffb97545.png&w=16&q=75) This course is completely beginners friendly.
This course is completely beginners friendly.
Skills You Will Learn
.ffb97545.png&w=16&q=75) Master the fundamentals of ethical hacking and penetration testing.
Master the fundamentals of ethical hacking and penetration testing..ffb97545.png&w=16&q=75) Learn how to identify system vulnerabilities and weaknesses.
Learn how to identify system vulnerabilities and weaknesses..ffb97545.png&w=16&q=75) Understand how to bypass security defenses using various tools.
Understand how to bypass security defenses using various tools..ffb97545.png&w=16&q=75) Acquire skills in network traffic analysis and packet sniffing.
Acquire skills in network traffic analysis and packet sniffing..ffb97545.png&w=16&q=75) Explore web application security and how to exploit vulnerabilities.
Explore web application security and how to exploit vulnerabilities..ffb97545.png&w=16&q=75) Understanding Python & AWS relevant to cybersecurity
Understanding Python & AWS relevant to cybersecurity.ffb97545.png&w=16&q=75) Deep dive into Information Systems Security Certification Professional
Deep dive into Information Systems Security Certification Professional.ffb97545.png&w=16&q=75) Gain proficiency in social engineering attacks and countermeasures.
Gain proficiency in social engineering attacks and countermeasures..ffb97545.png&w=16&q=75) Specialize into AWS Certified Security – Specialty
Specialize into AWS Certified Security – Specialty
Real-World Case Studies
Learn through real-world case studies

IT & Software
Network Security Case Study
A multinational corporation has experienced minor security breaches, raising concerns about their network. As a security consultant, assess vulnerabilities in their global infrastructure, and provide a report with actionable recommendations for improving security.

Finance
Web Application Security Case Study
A Finance startup is launching a platform for investments and transactions. As a security consultant, assess vulnerabilities, including authentication and third-party integrations. Provide a detailed report on risks, and offer remediation and security guidelines.

Healthcare
Incident Response and Forensics Case Study
A healthcare provider faces a data breach of patient records. As a cybersecurity expert, investigate the breach, identify how it occurred, contain the threat, and recover systems. Provide a report on the attack and advise on compliance and notifications.

for successfully completing the 'Cybersecurity with GenAI Career Track' course conducted from 17 May 2025 to 01 Nov 2025
Add a Industry Recognized
Certificate To Your Resume
Industry Recognized
Certificate
Learn the best from the best

Career Advancements
Elevate your career with a respected certificate

Industry Respect
Gain credibility in the field

Networking
Connect with experts and peers

Opportunities
Attract exciting job prospects and promotions


for successfully completing the 'Cybersecurity with GenAI Career Track' course conducted from 17 May 2025 to 01 Nov 2025

100% Moneyback Guarantee
Our Alumni Work Here

Frequently Bought Together
Get upto 90% OFF with Combo Offer below


AWS Solution Architect Micro Degree
₹188000
₹18800


DevOps Engineer
₹-151500
₹-15150
Total Fees
₹ 36500
₹ 3650
Get This Offer Now
Recommended MicroDegrees
Looking for help? Here are our most frequently asked questions
What is a EdYoda Micro Degree?
EdYoda Micro Degree is an online, Live classroom based short-term course, where you get Live Sessions conducted by industry experts. It is designed to help you acquire practical & job-relevant skills quickly.
How do I register for the micro degree?
To register, visit the micro degree details page and fill up the registration form and make the payment to reserve your seat before the application closing date.
What happens after I register and pay?
After successful registration and payment, you will receive a confirmation email with instructions on how to access the online micro degree classes
Are there any pre-requisites?
All you need is a PC or Laptop to attend the online live classes and your commitment of 4 weeks. Apart from that there are no prerequisite for the Micro Degree.
What if I miss a live session?
We've got you covered! The session recording will be added automatically on the classroom platform after the session is ended.
Will I get a certificate after completion?
Yes. After successful completion of curriculum you will be provided a digital certificate which you can download and share with others.

What is a EdYoda Micro Degree?
EdYoda Micro Degree is an online, Live classroom based short-term course, where you get Live Sessions conducted by industry experts. It is designed to help you acquire practical & job-relevant skills quickly.

How do I register for the micro degree?
To register, visit the micro degree details page and fill up the registration form and make the payment to reserve your seat before the application closing date.

What happens after I register and pay?
After successful registration and payment, you will receive a confirmation email with instructions on how to access the online micro degree classes

Are there any pre-requisites?
All you need is a PC or Laptop to attend the online live classes and your commitment of 4 weeks. Apart from that there are no prerequisite for the Micro Degree.

What if I miss a live session?
We've got you covered! The session recording will be added automatically on the classroom platform after the session is ended.

Will I get a certificate after completion?
Yes. After successful completion of curriculum you will be provided a digital certificate which you can download and share with others.
General FAQs
Everything you need to know














